Security Posture
Overview of the Security Posture Exercise
The Forward Enterprise Security Posture feature facilitates automated compliance and behavioral verification across various network segments, including single or multiple firewall zones, VRFs, and subnets. This capability is essential for maintaining a robust security stance within the network infrastructure.
Estimated Completion Time
15 minutes
Exercise 1: Setting Up the Security Posture Matrix
Objective: Navigate to the Security Posture Application and initiate the creation of a new Security Zone Matrix. This exercise aims to familiarize you with the setup process and the evaluation of network reachability within defined security zones.
-
Access Security Posture Application: Go to Security --> Posture on the Forward Enterprise platform.
-
Create New Matrix: Click on "Add New Matrix," provide a suitable name for the matrix, accept the default settings for other fields, and select "Add Resource Pools."
Exercise 2: Adding Security Zones to the Matrix
Objective: Add specific security zones to your newly created matrix for analysis. This step is crucial for mapping out the network's security landscape and identifying potential vulnerabilities.
Steps:
- Select Security zone for resource pool type.
- Select the device to add: Choose the firewall you wish to analyze, for example,
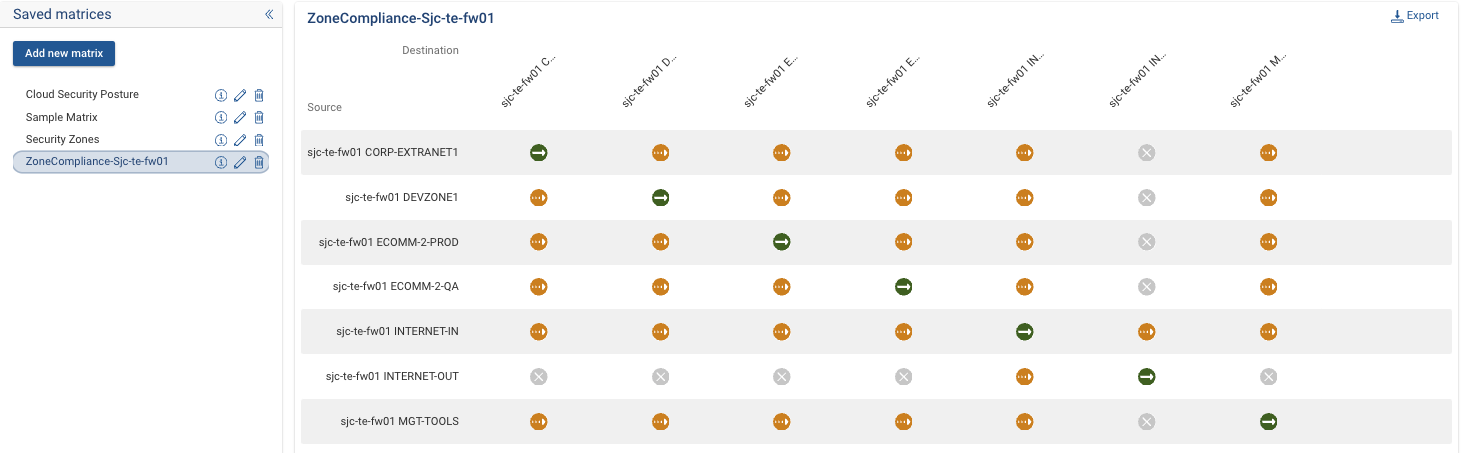
sjc-te-fw01. - Add Security Zones: Select all the zones presented and press "Done." Then, click on the "add" button to finalize the creation of the matrix.
Exercise 3: Analyzing Connectivity and Enforcement Points
Objective: Conduct a detailed analysis of connectivity within the security zones and investigate the enforcement points that allow or restrict connectivity. This exercise enhances your understanding of how security policies are applied within the network.
Steps:
- Hover Over Status Icons: Move the pointer over any of the status icons to note the ingress/egress zone and connectivity details.
- Access Connectivity Tables: Click on any icons of interest to view the detailed connectivity tables between resource containers.
- Investigate Enforcement Points: Select the magnifying glass icon to view a sample path and evaluate the enforcement points as demonstrated in the Path Search Function Testing section.
Key Insights
- Security Zone Matrix Evaluation: Learn how the security zone matrix continuously assesses reachability across configured source/destination zones, presenting the results through intuitive, color-coded status indicators for quick compliance assessment.
- Enhanced Security Insight: Gain valuable insights into the security posture of your network by analyzing connectivity details and enforcement points within the security zones.
- Proactive Security Management: The exercises provide a hands-on approach to managing and improving your network's security posture, enabling proactive identification and mitigation of potential security risks.